Towards a science of risk analysis
As HP Labs' Security Analytics research is commercialized, it readies for the cloud
The security analytics research team, from left to right: Yolanta Beres, Brian Monahan, Marco Casassa-Mont,
Simon Shiu, Richard Brown, Jonathan Griffin, Gareth Gale, and Stephen Crane.
By Simon Firth
Over the past year, HP's Enterprise Security Services (HP ESS) business has begun offering a new Security Analytics service to its customers. The University of Nottingham's IT center, for example, is using the product to make better decisions when it comes to maintaining the security of the institution's large IT network.
Employing Security Analytics "changed the way we think about information security," says Paul Kennedy, Group Leader for Security & Compliance at the university.

Senior Research
Manager Simon Shiu
The HP ESS service is based on research undertaken at HP's Cloud and Security Lab and represents an effort to set security planning on a more rigorous, scientific foundation, says Simon Shiu, who leads HPL's security research.
With businesses increasingly dependent on IT and also facing both elevated security threats and ever tighter budgets, chief information security officers are under severe pressure to align their security policies and investments with business priorities and risks. But that's more difficult than it sounds, Shiu argues, as traditional approaches that identify assets and vulnerabilities can quickly get divorced from the complex and dynamic IT environment in which those risks actually exist.
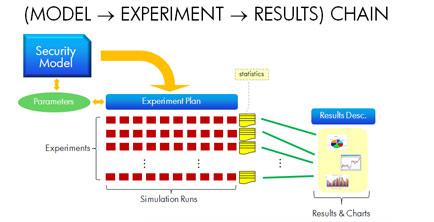
In response, Shiu and his colleagues have developed a way of modeling risks in the context of the complex systems in which they occur. Even in the discrete area of patching, for example, where software updates are issued to address newly discovered vulnerabilities, there are many concurrent processes and events occurring: vulnerabilities being discovered, malware spreading, patches being released, tested and deployed, anti-virus signatures being released and deployed, and so on.
The HP Labs models simulate such complex interactions and, as a result, offer security professionals a better understanding of the trade-offs they're making in prioritizing one approach to securing their networks over another. In addition, these models let IT managers explain their assumptions and decisions to other stakeholders, and also justify why they want to undertake a particular action to the executives in charge of their budgets.
The challenge of understanding how best to approach risk is a growing one, notes Shiu. As IT provision moves into the cloud, security managers will be relying more and more upon services that they don't necessarily own or control. In this newly complex and highly dynamic security environment, Shiu predicts, their need for clarity in approaching security risk is likely only to increase.
Analyzing security trade-offs
In moving towards a more scientific approach to risk analysis, the HP team first needed to understand how businesses themselves understand risk and how that understanding shapes the way in which they invest in security.*
A lot of what security managers do, the team soon realized, revolves around making trade-offs between different courses of action.
"In patching, for example," says Shiu, "one trade off is between patching aggressively and routinely affecting ‘planned' service levels or relaxing patching processes and then running a greater risk of emergencies and ‘unplanned' service disruptions. Beyond this there are trade-offs between the kind of mitigation and disruption you get with patching, versus relying on signatures, gateways and user policies."
The HP researchers developed these insights into a set of decision models which they tested in pilot programs with a major financial services company and a large public sector client.
As a result, says Shiu, "rather than thinking about their environment in the abstract, the security analysts in these organizations started to engage with the model and think about their strategy and the tradeoffs they were making."
"The process," Shiu notes, "gave them a way to justify their decisions to people who were not the same kind of stakeholders, and who didn't have the same kind of expertise as them."
The pilots were so successful that models for two kinds of security analysis – vulnerability threat management and identity and access management – were swiftly transferred to HP's Information Security business and made available to clients like Nottingham University.
Employing HP's Security Analytics models "showed us risk reduction opportunities we hadn't considered before and allowed us to see clearly where extra investment would gain us the most value," reports Nottingham's Paul Kennedy. "Equally importantly," he adds, "it highlighted simple process and policy changes that would have a big impact on our risk profile and pinpointed solutions that were ‘good enough' and that we shouldn't focus any further time or resources on."
Towards a science of security
Concurrent with their pilot modeling, the Labs team was researching how they might apply and integrate techniques from economics, psychology and human behavior into their modeling approach.
This led them to assemble a major research proposal for a project, called Trust Economics that would bring together cognitive scientists, psychologists, human behavior experts and economists from Bath University, Newcastle University and University College London, with HP's own researchers and security executives from Merrill Lynch and National Grid.
Led by HP researcher David Pym, now a professor at Aberdeen University, the project was awarded a major grant in 2009 by the U.K. government-backed Technology Strategy Board and was completed this summer. It generated multiple research papers on topics spanning human behavior, the economics of decision making, and mathematical modeling as well as a number of notable case studies of security decision making.
Security in the age of the cloud
As the Trust Economics project neared completion, however, it became clear that the environment in which IT security planning takes place was rapidly changing.
In particular, says Shiu, "We saw that the move to Cloud computing is completely disrupting the old lifecycle. You're now procuring IT from a supply chain rather than controlling it, and the threat environment is much more severe. "
Where IT managers once owned and controlled both their IT systems and the information contained in them, they were now increasingly reliant on multiple service providers to run their systems and manage that information. In consequence, says Shiu, it makes better sense to think about the whole system in which the information is residing – and as a result security becomes less a question of ownership and control than one of securing the proper stewardship of that information by others.
That's both a more complicated problem and a situation where it's even less wise to base your security planning and decision making on standard practices, the HP team felt. But it was still amenable to modeling, they believed, if they could better understand how people behave in this new environment.
To that end, Shiu's group, again working with David Pym, have launched a second research project, called Cloud Stewardship Economics, also funded by the Technology Strategy Board. It brings together economists from Bath and Aberdeen universities, the Institute of Information Security Professionals, the companies Validsoft, Sapphire, and Marmalade Box and insurer Lloyds of London in order to investigate the economics of security decisions in a cloud environment.
A major project focus is to treat the shift to cloud computing as a shift towards a complex eco-system of differently incentivized providers and consumers. By modeling the whole eco-system, and exploring both known and expected behaviors, the project aims to uncover potential information stewardship problems, and to help the different stakeholders (large and small enterprises, service providers and regulators) form strategies to improve overall security management.
In time, it's likely that these models will also migrate into HP's business units. In the nearer term, Shiu hopes to test them soon in workshops where players from across the cloud security landscape – in particular CIOs who are migrating, or planning to migrate, to cloud-based systems – will be invited to think in more depth about how to approach risk analysis and decision making in the cloud.
The wider HP Labs security research agenda
Risk analysis is just one phase in the much broader lifecycle of analysis, decision making, procurement, operations, monitoring, and then auditing of IT security.
"It's a cycle with which we see more and more organizations struggling," says Shiu, "and we're asking what difference can we make to it with our technology research?"
That's led HP's Cloud and Security Lab to also pursue research in trusted infrastructure (in particular, creating trusted virtualized platforms and exploiting them for better security management) and in the area of situational awareness.
Overall, says Shiu, "we are trying to seed some things out there that show how we can be more rigorous and scientific in our approach to security management."
* For more on this, see the report the team wrote for Lloyds of London on digital risk.